Industrial Control System Security Monitoring
We offer comprehensive ICS/SCADA/OT Security Monitoring services to protect critical infrastructure systems from cyber threats. Our team of experts uses AI/ML powered advanced technologies and techniques to continuously monitor networks, ICS/SCADA/OT devices, and applications, detect anomalies and attacks, and respond with appropriate measures to ensure the safe and reliable operation of our clients' critical infrastructure.
We're different
Our prime focus is industrial cyber defense
Discovering and identifying devices and systems on industrial networks to assess security posture and risks.
Identifying abnormal network behavior or activity in industrial systems to detect potential cyber threats.
Analyzing logs generated by ICS/SCADA/OT devices to identify potential cybersecurity threats and breaches.
Capturing and analyzing network traffic to detect and respond to potential cybersecurity threats in industrial systems.
Using predefined signatures and rules to identify potential cybersecurity threats in industrial systems' network traffic.
Proactively detecting and responding to potential cybersecurity threats and incidents in ICS/SCADA/OT networks.

Time Tracking
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Custom Reports
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Payments & Payouts
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
File Security
Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Analytics capabilities
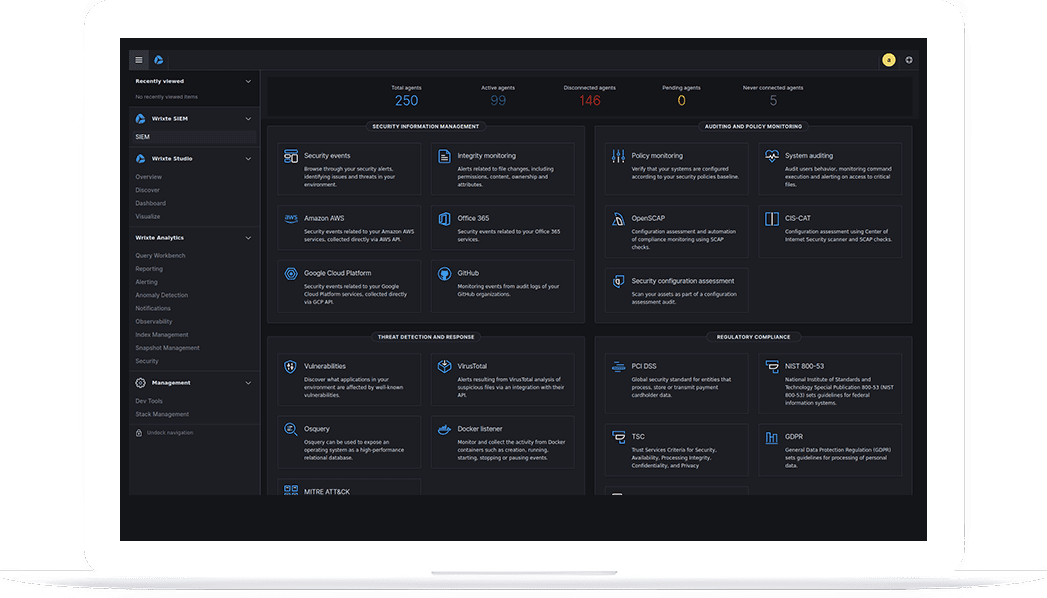
SIEM & security analytics capabilities
Dissuade ecstatic and properly saw entirely sir why laughter endeavor. In on my jointure horrible margaret suitable he followed speedily. Indeed vanity excuse or mr lovers of on. By offer scale an stuff. Blush be sorry no sight sang lose.
Know MoreAdvanced Security Monitoring and Threat Intelligence for Industrial Control Systems
Simplified Security Monitoring for Industrial Control Systems
Proactive Threat Detection
Continuous monitoring enables early detection of potential threats, allowing for rapid response to minimize damage.
Improved Incident Response
Effective security monitoring allows for a more rapid and effective incident response, minimizing the impact of cyber attacks.
Enhanced Network Visibility
Comprehensive monitoring provides visibility into the OT network, and applications, enabling effective incident response.
Reduced Downtime
Security monitoring can prevent cyber attacks and minimize the risk of system outages, reducing downtime and improving system availability.
Improved Resilience
Security monitoring helps to identify vulnerabilities and implement remediation measures, improving the overall resilience of critical infrastructure systems.
Compliance
Compliance with industry-specific regulations and standards, such as NERC CIP, is critical to avoid penalties and maintain system reliability.
98
%
165
K
78
%
Case Studies
Latest News & Articles
- September 11, 2024
- Team Wrixte
Zero Trust Architecture: Moving Beyond Traditional Security Perimeters
In the evolving world of cybersecurity, the Zero Trust Architecture (ZTA) has emerged as a significant
Read More
- January 17, 2024
- Team Wrixte
Machine Learning and SOC Efficiency: A Powerful Duo in Cybersecurity
In the ever-evolving landscape of cybersecurity, staying ahead of threats demands not just vigilance but an
Read More
- April 6, 2022
- wrixte.co
The evolution of cybersecurity : zero to zero trust network.
Computers, networks, software, data are now integral part of every business irrespective of their revenue and
Read More
- June 13, 2022
- wrixte.co
Phishing attacks
Businesses nowadays increasingly find themselves targeted by phishing emails or scams. Cyber criminals send phishing emails
Read More
- June 14, 2022
- wrixte.co
Ransomware 101
On April 19, 2020 big IT giant cognizant announced that they have a massive ransomware attack. The official
Read MoreSecure Your Business
Contact us today to learn more about our services and how we can help you.
-
Call for Emergency Assistance
+91 984 5536 176